Webhook Security
Webhook Security
Protecting requests
A publicly accessible URL is required so our webhook requests can be triggered.
HTTP Basic Authentication
Basic authentication is a simple authentication scheme built into the HTTP protocol. We recommend using it in your endpoints. You can configure your webhook URL by passing the username and password directly in the URL. Example: https://user:[email protected]/webhookd4sign
You may also use unique TOKENS to access your URL. Example: https://www.yoururl.com/webhookd4sign/TOKEN_SHA256
HTTPS Requests
Always use HTTPS endpoints.
HMAC
Introduction to HMAC
In cryptography, an HMAC is a specific type of message authentication code (MAC) involving a cryptographic hash function and a secret cryptographic key. As with any MAC, it may be used to simultaneously verify the data integrity and the authenticity of a message.
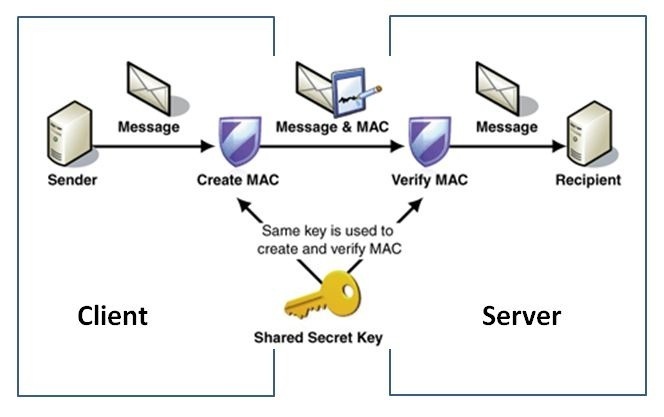
Every time a webhook is triggered, we calculate the SHA256 hash of the document UUID with the secret key and add this information to the header.
Example:
Content-Hmac: sha256=a683af9ffda69010bde886fc0e30ca8c257baf5f19ec875a1e0e36ddd92da944.
You must perform the same hash calculation to verify that the request came from D4Sign and that the data has not been compromised. Calculate the SHA256 hash of the document UUID together with the known secret key. The resulting value must match the one sent in the request header.
To generate your secret key, go to the API section of your account and click "Generate Secret Key MAC".
Tools to validate HMAC
https://www.freeformatter.com/hmac-generator.html
https://codebeautify.org/hmac-generator
https://www.liavaag.org/English/SHA-Generator/HMAC
Use these tools by entering the document UUID and your account’s secret key. The result must match the value received in the request header.
Mais referências sobre HMAC
Updated about 2 months ago